Phishing Simulations With Real-Life Scenarios
Phishing in NZ remains the top threat in almost all cyber statistics, and hybrid work environments and mobile increases the risk to your business.
We use real-world phishing simulation emails to train your employees.
What are Phishing Simulations?
Phishing simulations are controlled exercises designed to mimic real-life phishing attacks. These simulations are crafted to educate employees on recognising and responding to phishing attempts, a common method used by cybercriminals to steal sensitive information.
Keep Your Employees Engaged
It’s becoming increasingly important to provide phishing education to your employees. To ensure they are receiving regular, up-to-date training, consider running simulated phishing tests based on real-world phishing templates.
Our SecureAZ live phishing simulations will ensure you get the best value from your training. With our help, you can ensure your employees are better informed and prepared against malicious attacks.

Basic - Advanced Templates
We have put together a huge range of basic to advanced phishing templates that you can roll out to employees. Or if you are on a managed plan we will handle all this for you.

Custom Templates
As well as our library of templates, you can easily clone a template and customise it to however you like. You can change the title, from name, from email and personalise to your own company.

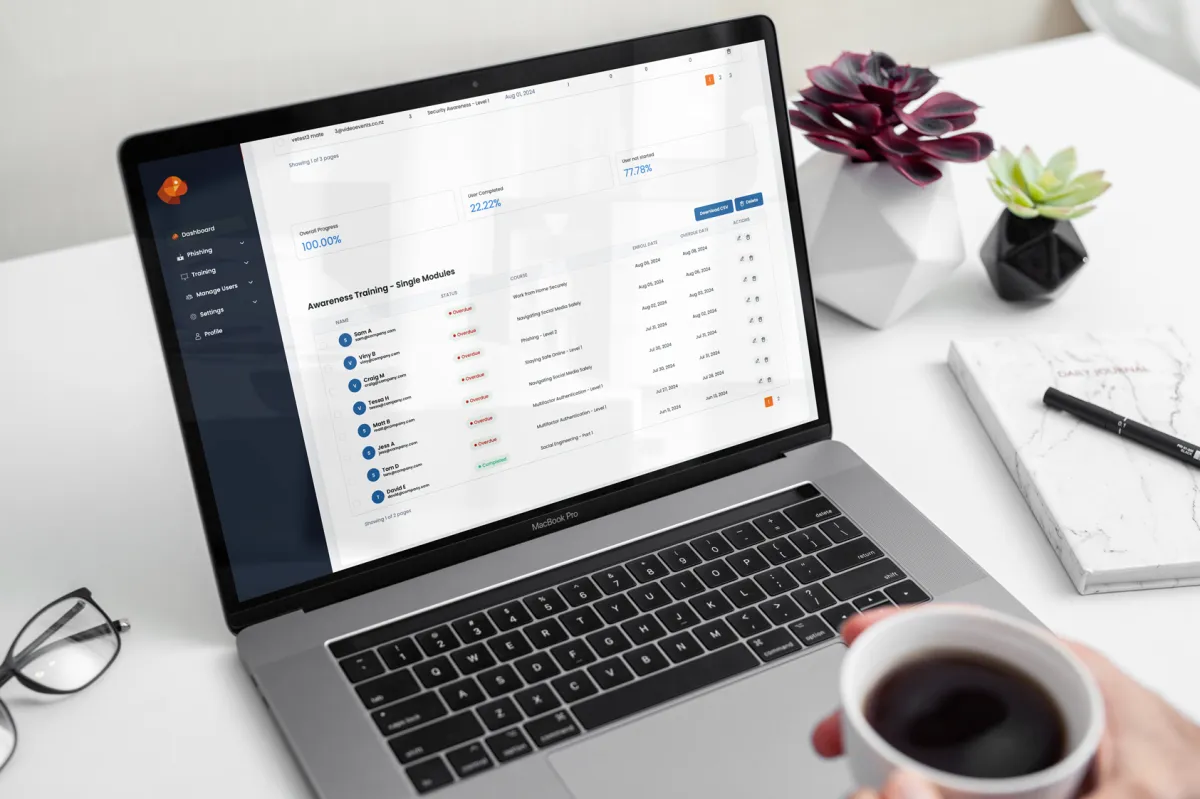
User progress reporting
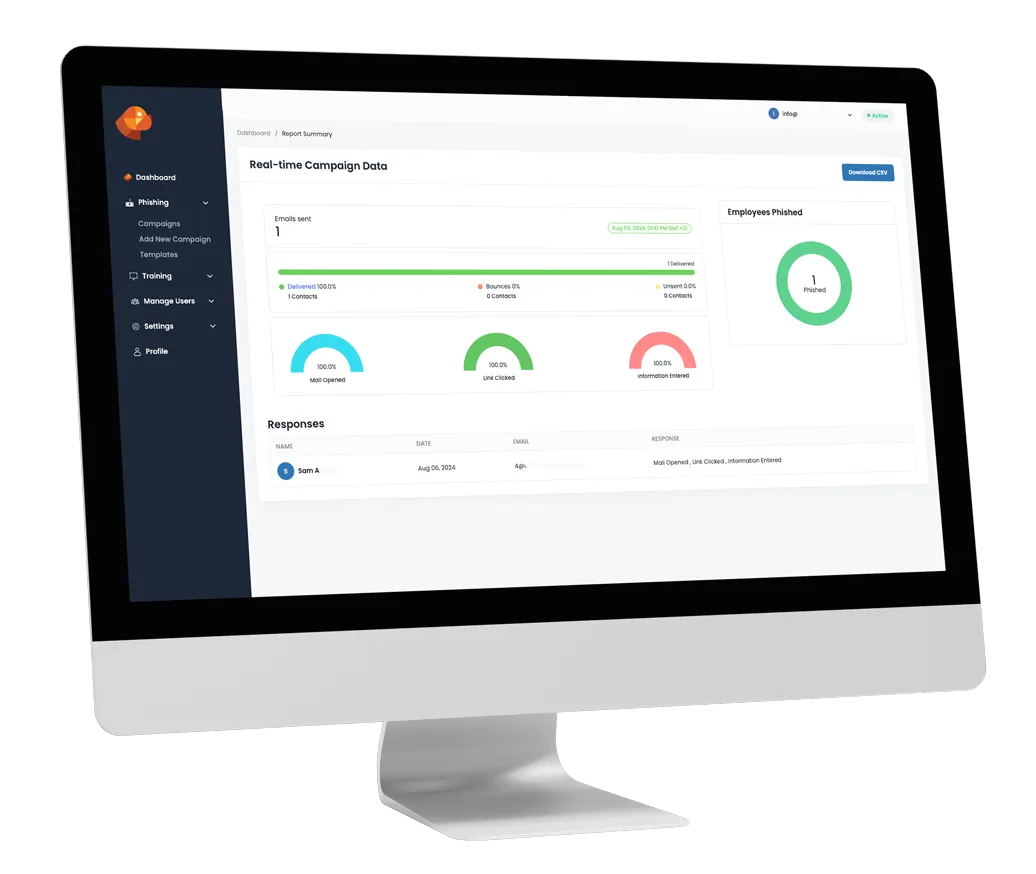
On your live dashboard you will see people clicking emails and entering in credentials. This is powerful information to act on immediately to protect your organisation.
Phishing Email Categories
Inland Revenue
Banking
Postal Services
Courier Services
Financial Services
Telecommunications
And More

Phishing Template Library
We have a selection of templates to use for your phishing campaign. These are all common Phishing scams and branded to replicate those common scams. Please note: the demo content displayed on this page all have fake logos for copyright reasons.
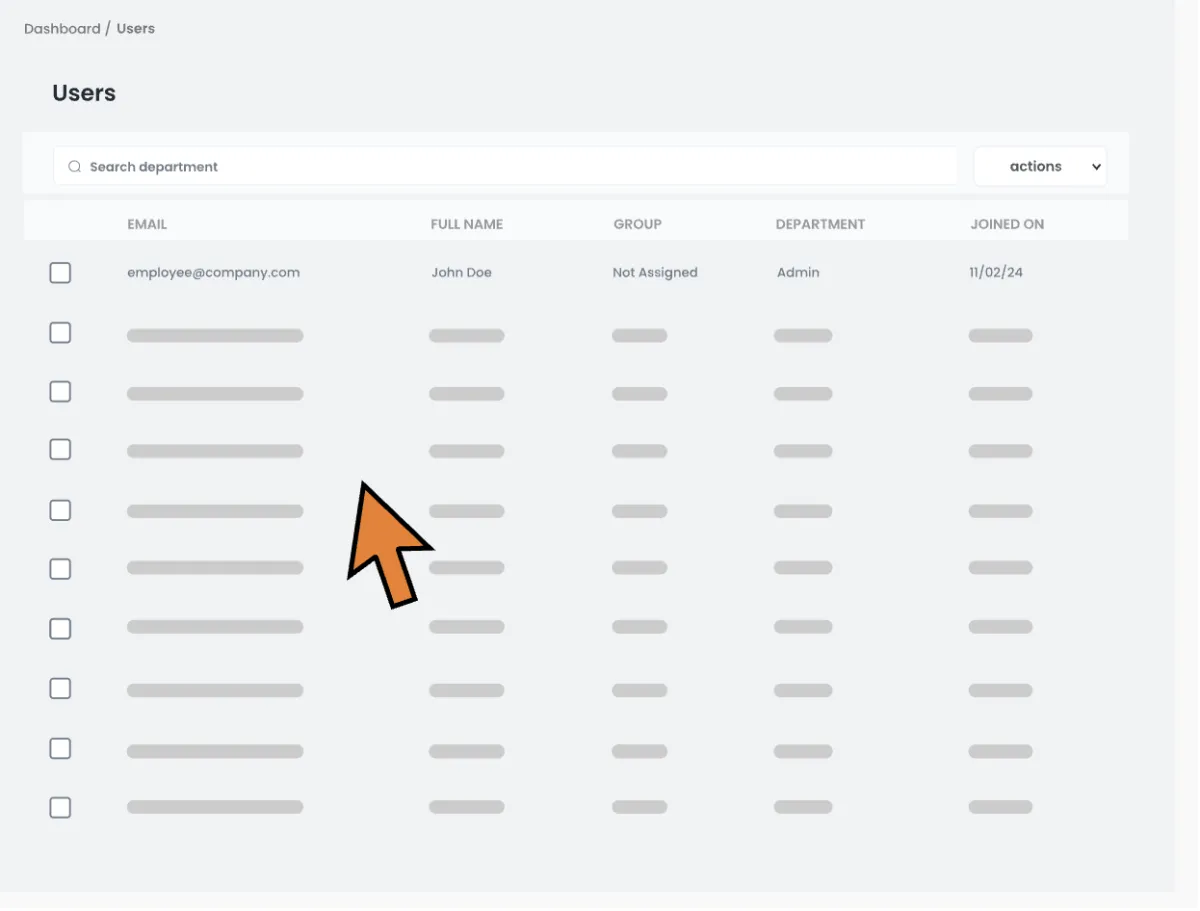
User Management
Your users are housed in the platform. You can sort them into groups how you like so you can do mass targeting campaigns.
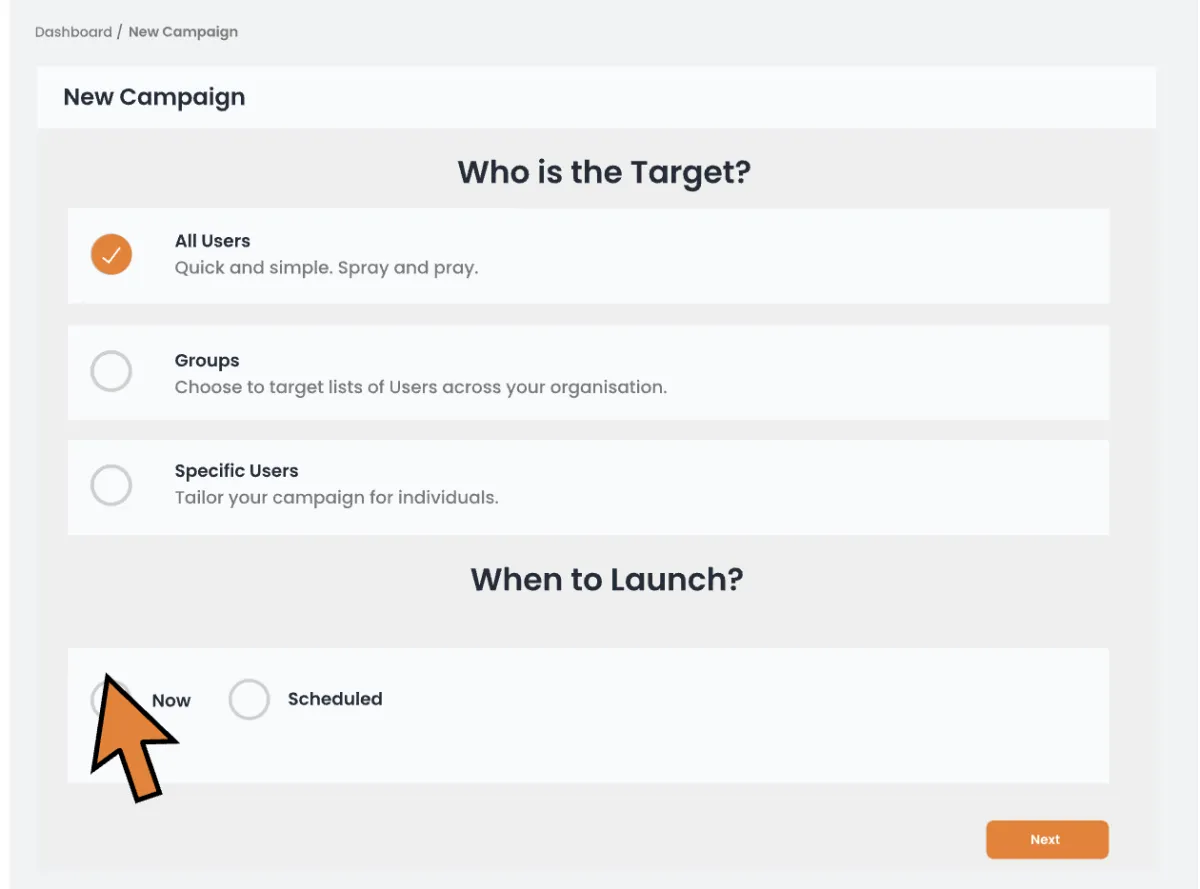
Send Out Fake Phishing Campaign
The SecureAZ Platform can fire out a one-off campaign or you can schedule a on-going plan.
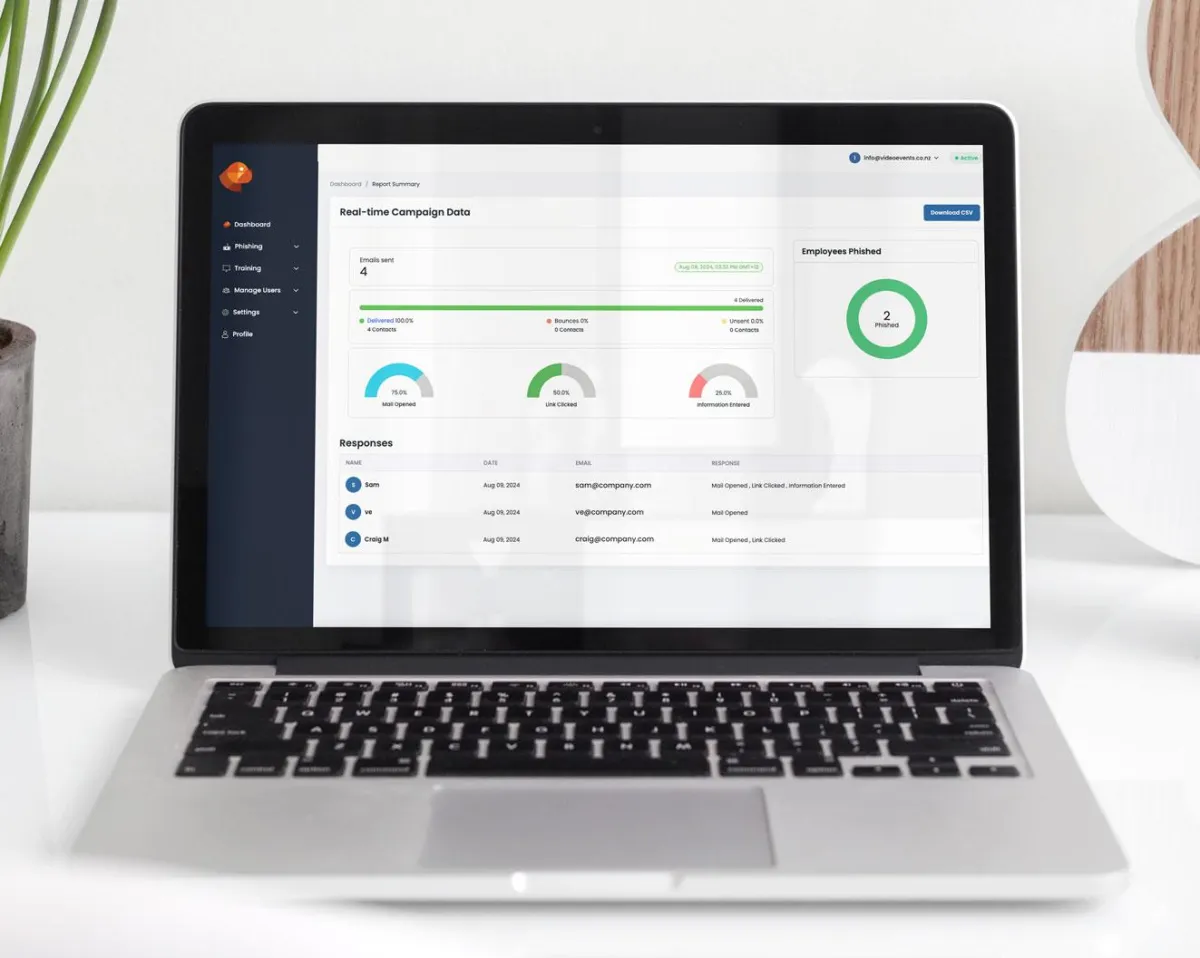
Get Valuable Data & Insights
You can see real-time data on email deliverability, bounced, opened, and even filled out.
Email Sent
Link Clicked
Details Filled Out
Real-time Reporting
During a phishing simulation, employees receive emails that closely resemble actual phishing emails, testing their ability to identify and avoid falling victim to such scams.
By conducting these simulations, organisations can assess their employees’ awareness and resilience against phishing threats.
The goal is to create a safer digital environment by improving the overall security posture of the company through continuous training and education.
Phishing simulations not only highlight vulnerabilities but also reinforce best practices, making employees the first line of defense in cybersecurity.
Success Stories
Hey Don't Take Our Words For It Hear From Our Client:
"Very happy with the team at SecureAZ. They are knowledgeable and informative, helped us navigate some good internal questions, and to plan for threats. They present real world examples that are specific and applicable to our business and have engaged all our staff with a clear cyber awareness message. We were very happy with their services."

Enabling Cybersecurity At Every Step
Many Australian companies struggle with employees in different departments who may not be equipped to identify cyber-security threats. We are here to bridge this gap with our comprehensive cyber-security training.



Easy as 1.. 2.. 3..
Our platform provides you with actionable data on the progress of your team’s security journey.
Our reports are user-friendly, simple to comprehend, and can be requested on-demand or you can receive a monthly report card via email.
SecureAZ Suite of Cyber Security Services







Give us a call or fill out our quote form and one of our friendly team will be in contact with you ASAP.
Popular Searches
Penetration Testing
Cyber Insurance Approved Training
Navigation
© 2025 SecureAZ Limited - All Rights Reserved.




